Security
Secure the Data, Not the Device
The Moka5 design principle assumes an un-trusted host. With Moka5 Enterprise AnyWare, the corporate workspace is separated from the host and runs within a secure container protected by AES256 encryption, 130+ security policies, integration with your existing security and access management solutions, and network access control – across Windows, Macs, bare metal and mobile devices.
In addition to keeping the bad guys from getting in, it is also prevents valuable data from getting out. The Moka5 container approach makes it possible to create a barrier around the corporate workspace where limits such as USB access, data movement between container and host, and other controls can be implemented. Moka5 also gives you the ability to disable access or wipe the container as needed.
Enforce the proper security measures by completely locking down a corporate environment without impacting how users configure and personalize their devices. How? With Moka5’s secure container for PCs and Macs.


Remote Worker Security





Secure Remote Access
While Moka5 solutions are based on a unified architecture, there are of course distinct differences between PC and mobile OS’s. Let’s take a look at the additional security measures implemented to address each platform’s unique needs.
Windows Protections
While IT has long since given up wresting control of the desktop from end users, a Windows image in a secure container is a different story. Here, politically, it’s possible to withhold admin privileges, implement stringent security configurations, and tightly control software installations and updates.
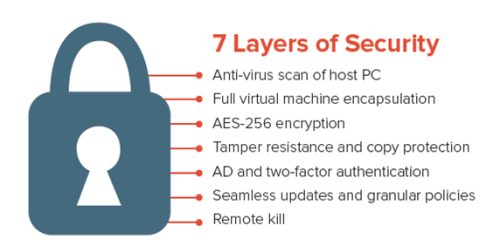
Built-in AVG anti-virus constantly monitors for key loggers and screen scrapers, and ensures these are not present on the host computer at startup
Policy-enforced container keeps corporate data separate from personal files
AES 256 encryption of the container ensures compliance with data security standards and privacy regulations
Tamper-resistance and copy protection keeps the virtual desktop from being moved or edited
LDAP/AD integration, two-factor authentication support ensures that you can use your existing access control processes
130+ granular security policies give IT full control over the container
Remote revoke or kill allows you to wipe the encrypted container from lost or stolen devices over the Internet or through a timeout mechanism
Mobile Protections
Users consume corporate data from their mobile devices on the go: accessing web apps, reading a PDF file, reviewing a word doc or PowerPoint presentation. Moka5 allows them to be connected to critical corporate information and apps at all times – working offline or securely online without the need for a VPN client.
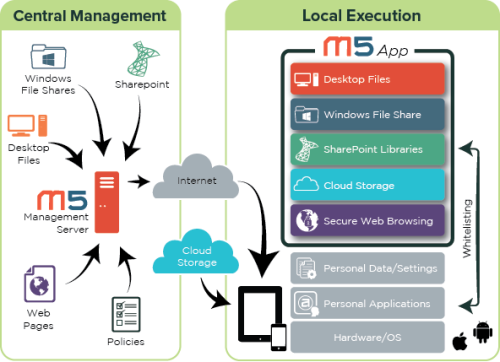
M5 is the only iOS solution that offers you enterprise-class security and management, offline use, secure web browser, and an intuitive native interface for browsing SharePoint and Intranet files without needing a VPN connection. Here’s how it works:
Active Directory (AD) integration for user authentication. Existing AD access permissions determine individual users’ access to Windows file shares
Moka5 ticketing authentication mechanism ensures that only authorized devices can connect to internal network resources
Secure browsing of internal web apps without a VPN client on an iOS device
Remotely revoke or wipe LiveData on a lost or stolen iOS device
Encrypted network traffic (sent as http over SSL) prevents man-in-the-middle attacks
Encrypted data on local storage – secure data using AES-128 encryption
Data segregation with layering separates corporate data and internal web apps from personal data, settings, and apps